
Like many things in the shadowy world of cyber-crime, an insider threat is something very few people have experience of.
Even fewer people want to talk about it.
But I was given a unique and worrying experience of how hackers can leverage insiders when I myself was recently propositioned by a criminal gang.
“If you are interested, we can offer you 15% of any ransom payment if you give us access to your PC.”
That was the message I received out of the blue from someone called Syndicate who pinged me in July on the encrypted chat app Signal.
I had no idea who this person was but instantly knew what it was about.
I was being offered a portion of a potentially large amount of money if I helped cyber criminals access BBC systems through my laptop.
They would steal data or install malicious software and hold my employer to ransom and I would secretly get a cut.
I had heard stories about this kind of thing.
In fact, only a few days before the unsolicited message, news emerged from Brazil that an IT worker there had been arrested for selling his login details to hackers which police say led to the loss of $100m (£74m) for the banking victim.
I decided to play along with Syndicate after taking advice from a senior BBC editor. I was eager to see how criminals make these shady deals with potentially treacherous employees at a time when cyber-attacks around the world are becoming more impactful and disruptive to everyday life.
I told Syn, who had changed their name mid-conversation, that I was potentially interested but needed to know how it works.
They explained that if I gave them my login details and security code then they would hack the BBC and then extort the corporation for a ransom in bitcoin. I would be in line for a portion of that payout.
They upped their offer.
“We aren’t sure how much the BBC pays you but what if you took 25% of the final negotiation as we extract 1% of the BBC’s total revenue? You wouldn’t need to work ever again.”
Syn estimated that their team could demand a ransom in the tens of millions if they successfully infiltrated the corporation.
The BBC has not publicly taken a position on whether or not it would pay hackers but advice from the National Crime Agency is not to pay.
Still, the hackers continued their pitch.
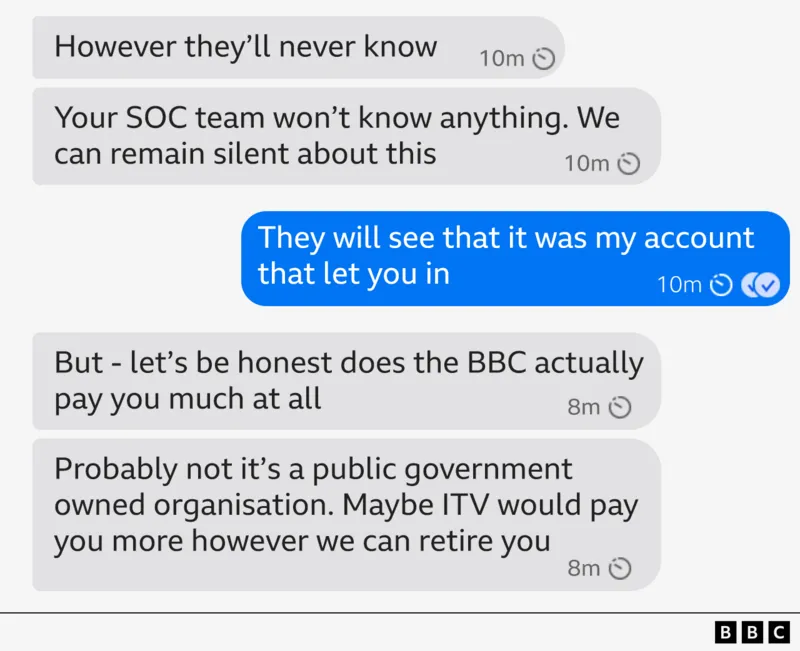
Syn said I would be in line for millions. “We would delete this chat for you to never be found,” they insisted.
The hacker claimed they had lots of success with striking deals with insiders in previous attacks.
The names of two companies that got hacked this year were shared as examples of when a deal was struck – a UK healthcare company and a US emergency services provider.
“You’d be surprised at the number of employees who would provide us access,” Syn said.
Syn said he was a “reach out manager” for the cyber-crime group called Medusa. He claimed to be western and the only English speaker in the gang.
Medusa is a ransomware-as-a-service operation. Any criminal affiliate can sign up to its platform and use it to hack organisations.
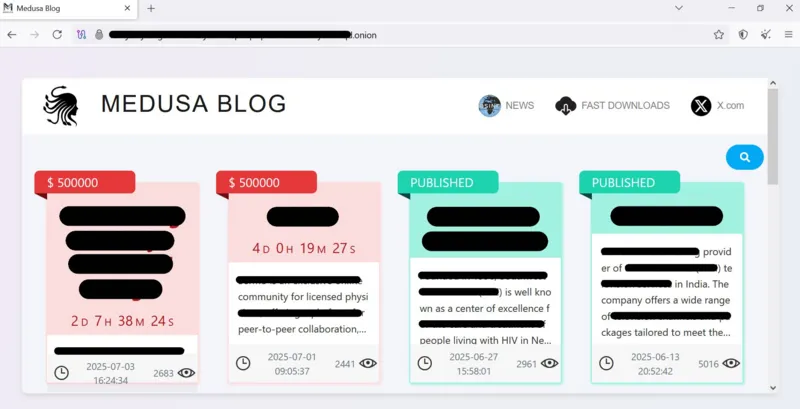
According to a research report from cyber-security firm CheckPoint, Medusa’s administrators are thought to operate out of Russia or one of its allied states.
“The group avoids targeting organisations within Russia and the Commonwealth of Independent States and [its activity is predominantly] on Russian-language dark web forums.”
Syn proudly sent me a link to a US public warning about Medusa which was put out in March. US cyber authorities said that in the four years that the group has been active, it has hacked “more than 300 victims”.
Syn insisted they were serious about making a deal to secretly sell the keys to my corporation’s kingdom in exchange for a hefty pay day.
You never really know who you are talking to though so I asked Syn to prove it. “You could be kids messing about or someone trying to entrap me,” I suggested.
They replied with a link to Medusa’s darknet address and invited me to contact them through the group’s Tox – a secure messaging service loved by cyber criminals.
Syn was very impatient and ramped up the pressure on me to reply.
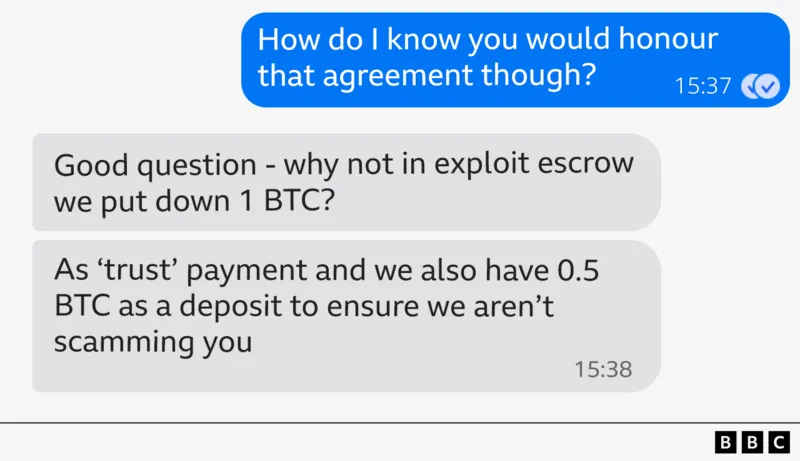
They sent a link to Medusa’s recruitment page on an exclusive cyber-crime forum urging me to start the process of securing 0.5 bitcoin (about $55,000) in a deposit arrangement.
This was effectively them guaranteeing me this money at a minimum once I handed over my login details.
“We aren’t bluffing or joking – we don’t have a purpose media wise we are only for money and money only and one of our main managers wanted me to reach out to you.”
They apparently chose me because they assumed I was technically minded and have high-level access to BBC IT systems (I do not). I’m still not entirely sure that Syn knew I was a cyber correspondent and not a cyber security or IT employee.
They asked me lots of questions about the BBC IT network that I wouldn’t have answered even if I knew. They then sent a complicated jumble of computer code and asked me to run it as a command on my work laptop and report back what it said. They wanted to know what internal IT access I had to start planning their next steps once inside.
At this point I had been talking to Syn for three days and I decided I had taken it far enough and needed some extra advice from the BBC’s information security experts.
It was Sunday morning so my plan was to talk to my team the next morning.
So I stalled for time. But Syn got annoyed.
“When can you do this? I’m not a patient person,” the hacker said.
“I guess you don’t want to live on the beach in the Bahamas?” they pressured.
They gave me a deadline of midnight on Monday. Then they ran out of patience.
My phone started pinging with two-factor authentication notifications. The pop-ups were from the BBC’s security login app asking me to verify that I was trying to reset the password to my BBC account.
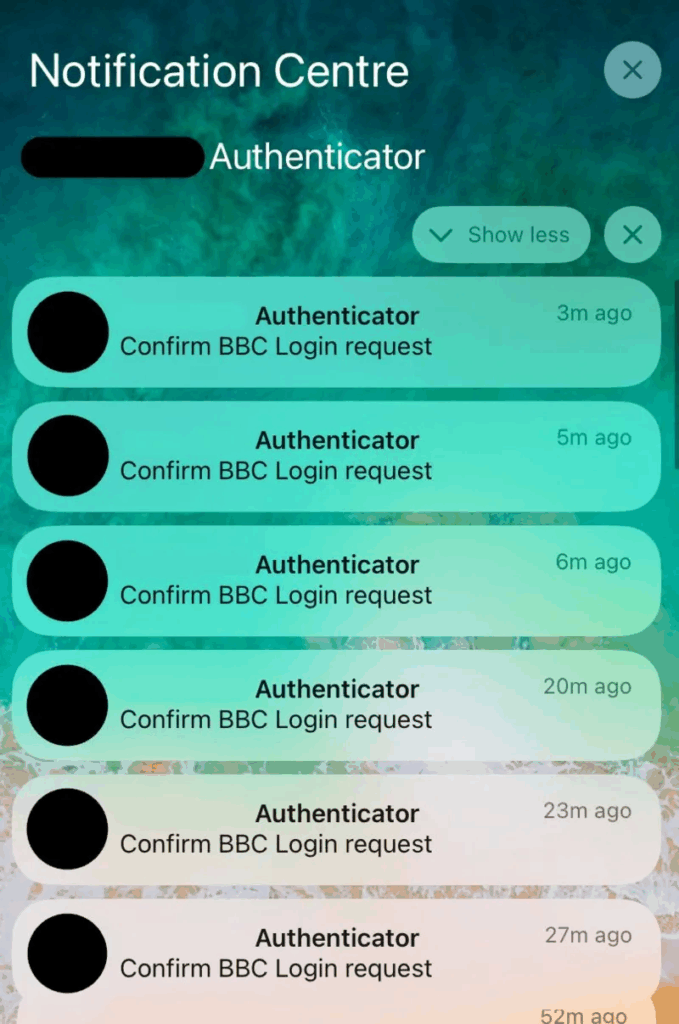
As I held my phone in my hands, the screen filled with a new request every minute or so.
I knew exactly what this was – a hacker technique known as MFA bombing. Attackers bombard a victim with these pop ups by attempting to reset a password or login from an unusual device.
Eventually the victim presses accept either by mistake or to make the pop-ups go away. This is famously how Uber was hacked in 2022.
Being on the receiving end was unsettling.
The criminals had taken the relatively professional conversation out of the safety of my chat app to my phone home screen. It felt like the equivalent of having criminals aggressively knocking on my front door.
I was confused at the change of tactic but too cautious to open up my chats with them in case I accidentally clicked accept. This would have given the hackers immediate access to my BBC accounts.
The security system would not have flagged it as malicious as it would have looked like a normal login or password reset request from me. After that the hackers could have begun searching out access to sensitive or important BBC systems.
As a reporter and not an IT worker, I don’t have high level access to BBC systems but it was still worrying and effectively meant my phone was unusable.
I called the BBC information security team and as a precaution we agreed to disconnect me from the BBC entirely. No emails, no intranet, no internal tools, no privileges.
The bizarrely calm message from the hackers came later that evening.
“The team apologises. We were testing your BBC login page and are extremely sorry if this caused you any issues.”
I explained that I was now locked out of the BBC and was annoyed. Syn insisted that the deal was still there if I wanted it. But after I didn’t respond for a few days, they deleted their Signal account and disappeared.
I was eventually reinstated to the BBC system albeit with added protections to my account. And with the added experience of being on the inside of an insider threat attack.
A chilling insight into the ever-evolving tactics of cyber criminals and one that has highlighted a whole area of risk to organisations that I didn’t truly appreciate until I myself was on the receiving end.